What is Two-factor Authentication (2FA)?
Before we begin, let’s see what 2FA is. You know that you have to enter a password to log into your account. Without the correct password, you cannot log in. 2FA is the process of adding an extra security layer to your account. After enabling it, you cannot log into your account by entering the password only. You have to complete one more security step. This means in 2FA, the website verifies the user in two steps. Read: How to Enable 2-step Verification in Microsoft Account.
How Does 2FA Work?
Let’s understand the working principle of two-factor authentication. The 2FA requires you to verify yourself two times. When you enter your username and password, you will be redirected to another page, where you have to provide a second proof that you are the real person trying to log in. A website can use any of the following verification methods:
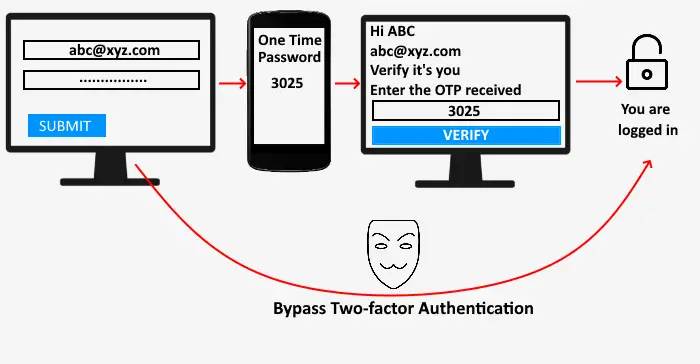
OTP (One Time Password)
After entering the password, the website tells you to verify yourself by entering the OTP sent on your registered mobile number. After entering the correct OTP, you can log into your account.
Prompt Notification
Prompt notification is displayed on your smartphone if it is connected to the internet. You have to verify yourself by tapping on the “Yes” button. After that, you will be logged into your account on your PC.
Backup Codes
Backup codes are useful when the above two methods of verification won’t work. You can log into your account by entering any one of the backup codes you have downloaded from your account.
Authenticator App
In this method, you have to connect your account with an authenticator app. Whenever you want to log into your account, you have to enter the code displayed on the authenticator app installed on your smartphone. There are several more methods of verification that a website can use. Read: How To Add Two-step Verification To Your Google Account.
How Hackers can get around Two-factor Authentication
Undoubtedly, 2FA makes your account more secure. But there are still many ways by which hackers can bypass this security layer.
1] Cookie Stealing or Session Hijacking
Cookie stealing or session hijacking is the method of stealing the session cookie of the user. Once the hacker gets success in stealing the session cookie, he can easily bypass the two-factor authentication. Attackers know many methods of hijacking, like session fixation, session sniffing, cross-site scripting, malware attack, etc. Evilginx is among the popular frameworks that hackers use to perform a man-in-the-middle attack. In this method, the hacker sends a phishing link to the user that takes him to a proxy login page. When the user logs into his account using 2FA, Evilginx captures his login credentials along with the authentication code. Since the OTP expires after using it and also valid for a particular time frame, there is no use in capturing the authentication code. But the hacker has the user’s session cookies, which he can use to log into his account and bypass the two-factor authentication.
2] Duplicate Code Generation
If you have used the Google Authenticator app, you know that it generates new codes after a particular time. Google Authenticator and other authenticator apps work on a particular algorithm. Random code generators generally start with a seed value to generate the first number. The algorithm then uses this first value to generate the remaining code values. If the hacker is able to understand this algorithm, he can easily create a duplicate code and log into the user’s account.
3] Brute Force
Brute Force is a technique to generate all the possible password combinations. The time for cracking a password using brute force depends on its length. The longer the password is, the more time it takes to crack it. Generally, the authentication codes are from 4 to 6 digits long, hackers can try a brute force attempt to bypass the 2FA. But today, the success rate of brute force attacks is less. This is because the authentication code remains valid only for a short period.
4] Social Engineering
Social Engineering is the technique in which an attacker tries to trick the user’s mind and forces him to enter his login credentials on a fake login page. No matter whether the attacker knows your username and password or not, he can bypass the two-factor authentication. How? Let’s see: Let’s consider the first case in which the attacker knows your username and password. He cannot log into your account because you have enabled 2FA. To get the code, he can send you an email with a malicious link, creating a fear in you that your account can be hacked if you do not take immediate action. When you click on that link, you will be redirected to the hacker’s page that mimics the authenticity of the original webpage. Once you enter the passcode, your account will be hacked. Now, let’s take another case in which the hacker does not know your username and password. Again, in this case, he sends you a phishing link and steals your username and password along with the 2FA code.
5] OAuth
OAuth integration provides users with a facility to log into their account using a third-party account. It is a reputed web application that uses authorization tokens to prove identity between the users and service providers. You can consider OAuth an alternate way to log into your accounts. An OAuth mechanism works in the following way: In the above processes, we have seen that the attacker does not require to verify himself via 2FA. But for this bypass mechanism to work, the hacker should have the user’s account username and password. This is how hackers can bypass the two-factor authentication of a user’s account.
How to prevent 2FA bypassing?
Hackers can indeed bypass the two-factor authentication, but in each method, they need the users’ consent which they get by tricking them. Without tricking the users, bypassing 2FA is not possible. Hence, you should take care of the following points:
Before clicking on any link, please check its authenticity. You can do this by checking the sender’s email address.Create a strong password that contains a combination of alphabets, numbers, and special characters.Use only genuine authenticator apps, like Google authenticator, Microsoft authenticator, etc.Download and save the backup codes at a safe place.Never trust phishing emails that hackers use to trick the users’ minds.Do not share security codes with anyone.Setup security key on your account, an alternative to 2FA.Keep changing your password regularly.
Read: Tips to Keep Hackers out of your Windows computer.
Conclusion
Two-factor authentication is an effective security layer that protects your account from hijacking. Hackers always want to get a chance to bypass 2FA. If you are aware of different hacking mechanisms and change your password regularly, you can protect your account better.